DNS Threats
By: Trinity Security Technical Assurance Team
Today’s threat actors are utilising DNS TXT records to gather a comprehensive list of cloud-based service providers used by an organisation. This allows threat actors to broaden their attack surface and launch more focused phishing campaigns. These campaigns are often the gateway to enterprise breaches or ransomware attacks. All of the top ransomware as a service (RaaS) providers review these external services (MITRE Att8ck T1133) before tailoring their attack.
Domain Name System (DNS) is a critical component of the internet infrastructure that translates domain names into IP addresses. Due to its importance, it has been a prime target of various cyberattacks, including enumeration and brute-forcing attacks. Enumeration attacks on DNS involve querying a DNS server for information about a domain, such as its subdomains, mail servers, and hostnames. Threat actors can use this information to map the network, identify potential targets, and launch further attacks such a phishing campaigns.
Classic brute-forcing attacks on DNS involve trying to guess the domain names or subdomains by systematically generating and testing combinations of letters, numbers, and symbols. Attackers can use a variety of tools and techniques, such as wordlists, permutations, and fuzzing, to automate and speed up the process. DNS enumeration and brute-forcing attacks have been around since the early days of the internet, but they have become more sophisticated and widespread over time. In the late 1990s and early 2000s, many DNS servers were vulnerable to zone transfer attacks, which allowed attackers to obtain a complete copy of the DNS database for a domain. This could provide valuable information for reconnaissance.
DNS TXT Records
DNS TXT records are a type of Domain Name System (DNS) resource record used to store arbitrary text data. They were originally created to allow domain owners to add descriptive information to their DNS records, such as human-readable notes, copyright information, and usage policies. TXT records can also be used for various other purposes, such as verifying domain ownership which is what we will focus on here, configuring email services, and publishing DomainKeys Identified Mail (DKIM) and Sender Policy Framework (SPF) records for email authentication.
One of the most common uses of TXT records today is for domain verification in the context of online services, such as Google Search Console, Cloud SaaS providers, and other web analytics and marketing tools. To verify domain ownership, these services require domain owners to add a unique TXT record to their DNS configuration, which includes a verification token or code provided by the service. Once the TXT record is added and propagated across the DNS infrastructure, the service can check for its presence and verify domain ownership.
Our Analysis
Trinity reviewed the top 500 domains visited by Australians according to alexa.com. Using this list it was possible to extract all of the available DNS TXT records associated with the domains. The results are as follows:
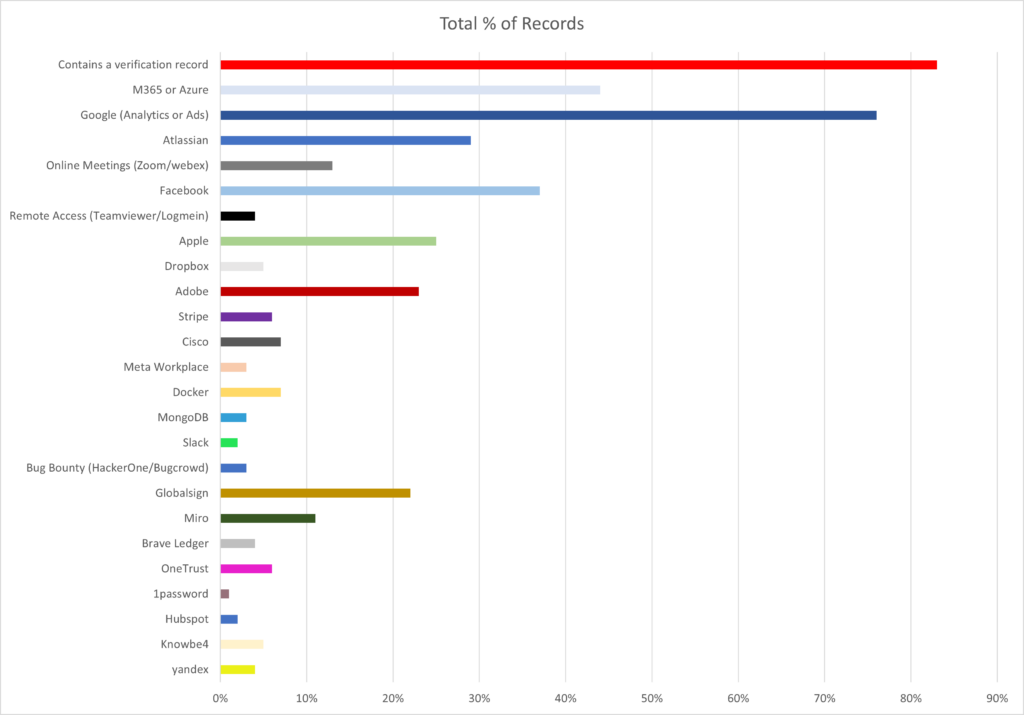
Over 80% of all domains analysed contained at least one DNS TXT record containing a legacy verification record, while 58% of all TXT records analysed were related to verification tokens. Before reviewing the records in detail it was evident that Microsoft, Google and Apple would be at the top of the list, but the other vendors provide a far more nuanced attack surface for threat actors to abuse. These records are a significant amount of vendor information being exposed to the internet which is no longer required to be kept beyond the verification event. This list is not complete but it does also highlight the portion of service providers using this method to verify domain ownership.
Given the above statistics we can see why threat actors choose particular platforms for their phishing campaigns and how they may target specific businesses by reviewing these TXT records. The following specific examples for a portion of the TXT records above have been circulating across the internet with varying levels of success:
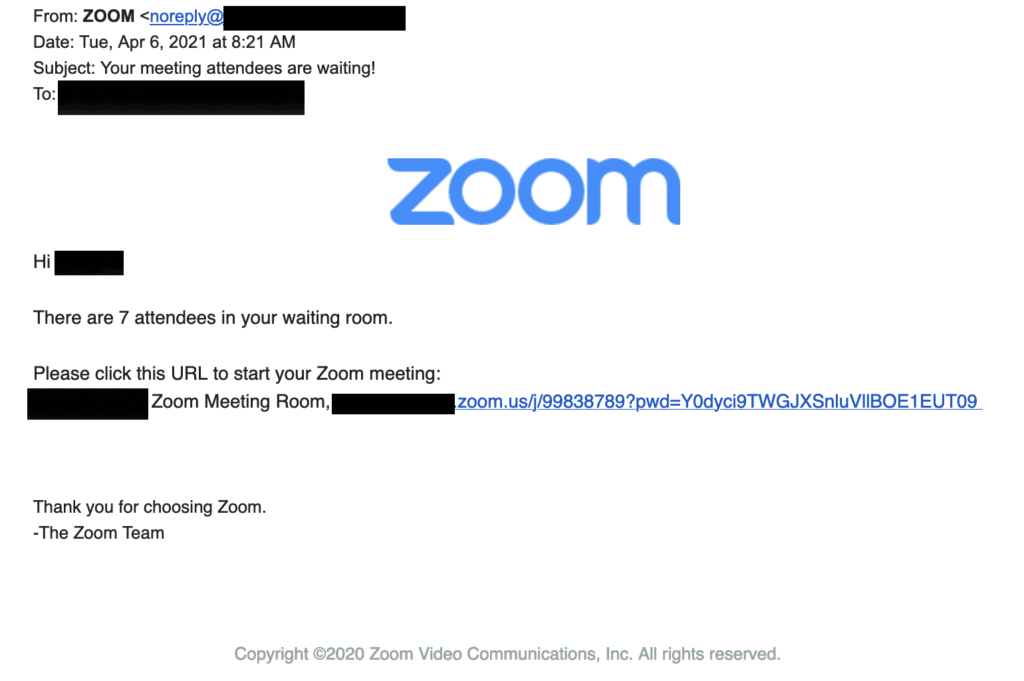
Zoom:
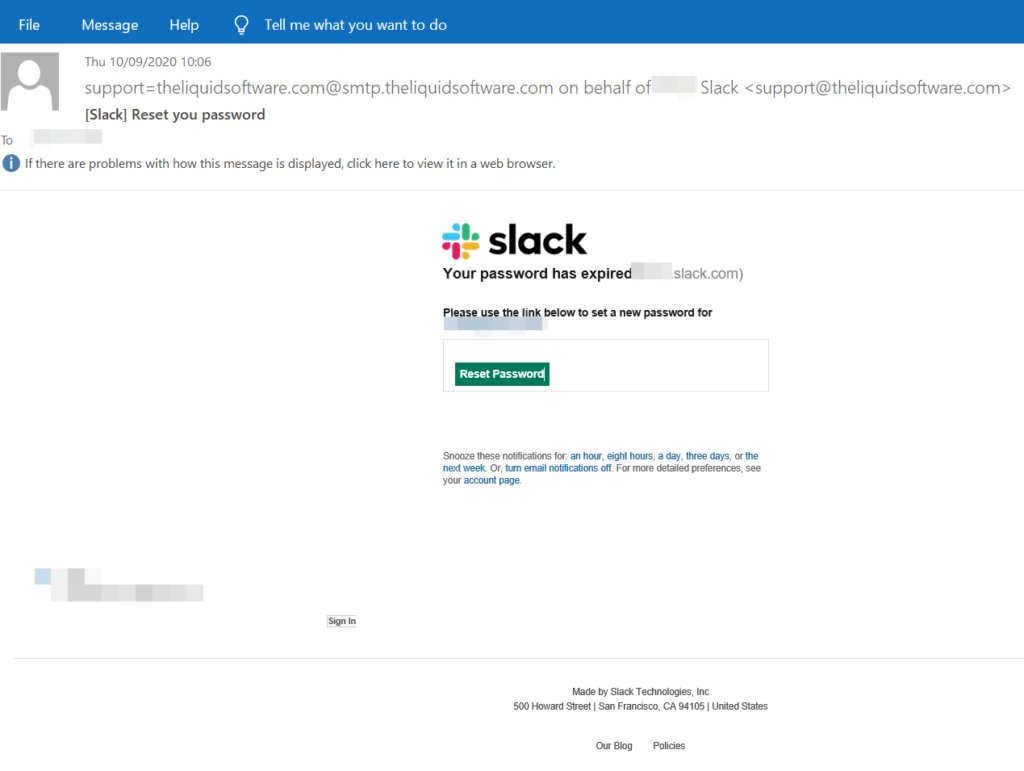
Dropbox:
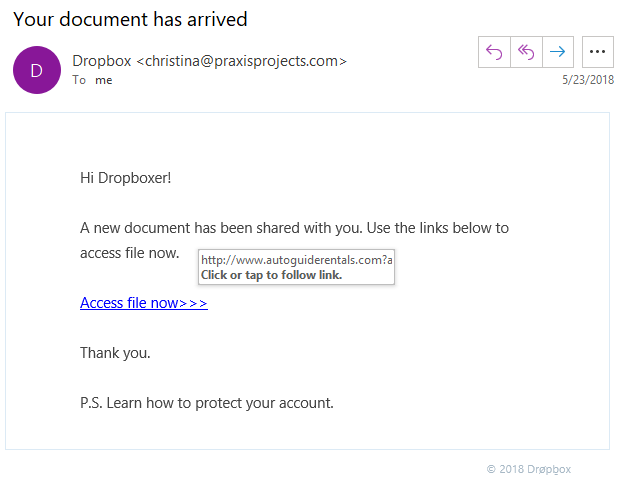
Slack:
Conclusion
Domain Name System (DNS) records are a crucial aspect of domain verification ownership, providing a reliable and secure way for domain owners to authenticate their identity and authorise access to various online services. DNS TXT verification records, in particular, have become a popular method for domain verification, allowing domain owners to publish unique tokens or codes in the DNS configuration that can be used to verify ownership.
However, it is essential to consider the potential security risks and privacy concerns associated with leaving verification records in the DNS configuration after verification is complete. Verification records can expose sensitive information to potential attackers, increasing the risk of unauthorised access, phishing, and other cyber threats. Additionally, verification records can cause clutter and potential conflicts with other DNS records, leading to unintended consequences that may affect the reliability and availability of the domain or service.
To minimise these risks, it is recommended that domain owners delete DNS TXT verification records after they have been successfully verified. This can help prevent unauthorised access, reduce the risk of errors or conflicts, and protect a businesses privacy by removing sensitive or platform identifiable information from the records. We would also encourage these cloud vendors to request the deletion of these tokens once the verification is complete, we are aware of a handful of providers that currently do this.
If you or your business has any concerns or queries about their records, there are a multitude of free services online that can display the records that are currently publicly visible on the internet or Trinity can assist with detecting and removing these as part of a wider perimeter security review. At Trinity Cyber Security, this is one aspect of the many activities that we carry out in most engagements and call it as a basic Hygiene, regardless of the inherent immediate technical risk.
We strive to continually help improve the cyber security posture for an organisation, please reach out to us at [email protected]. We will set up at a convenient time to understand more about your business and the areas for consideration from our experience working in the industry for over 15+ years.
Leave a Reply