Introduction
Given the increasing publicity around the Essential Eight, many organisations may have already undertaken an assessment, and adhere to a particular maturity level. Subsequently, a target maturity level is decided upon, a gap assessment is performed, and a roadmap of activities to achieve the target level is developed.
Roadmaps are tremendously useful in ensuring that work is coherently directed towards a well-defined outcome. However, as with many of these types of artifacts, they are developed with imperfect information, and may not offer the best path forward for an organisation looking to improve security.
Problems with Roadmaps
Roadmaps are tremendously useful in ensuring that work is coherently directed towards a well-defined outcome. However, as with many of these types of artifacts, they are developed with imperfect information, and may not offer the best path forward for an organisation looking to improve security.
Organisations may be experiencing one of two extremes when considering how to develop a roadmap.
Paralysis by analysis – Attempting to achieve optimal information and performing endless analysis, resulting in little actual work towards realising any goals.
“Low-hanging fruit” or “getting runs on the board” – Immediately actioning as many of the easy to achieve outcomes as possible to build momentum. Commendable as this may be, it could very well be building momentum in entirely the wrong direction.
Pragmatic Idealisms
Perhaps there is a middle ground that might be more appropriate. Striking a balance between blindly charging forward and endless vacillation. At Trinity Cyber Security, we understand that each organisation is unique, and we take a lot into account when developing roadmaps.
These two items are among some of the key factors we consider:
1. Undertaking information producing work packages first.
If there is a list of uplift tasks to do, then first do activities whose outcomes provide additional information. Use this information to organise the remainder of the roadmap.
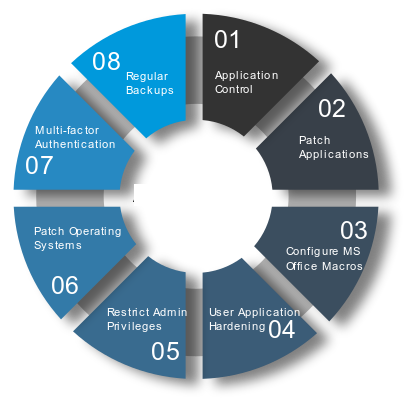
There is a great example of one of these in the Essential Eight. The very first strategy requests the following:
“An automated method of asset discovery is used at least fortnightly to support the detection of assets for subsequent vulnerability scanning activities.”
Any good asset discovery platform is undoubtedly going to provide huge amounts of context about organisational assets that can be used to understand what work should be prioritised, and where effort should be focused. It may even be deemed more appropriate to split up work packages to initially cover higher-value assets and then come back and cover lower-value assets.
2. Understanding the implications of work packages in the wholistic program of works.
Understand what can be aggregated into larger packages, or what outcomes can be achieved through the deployment of a single tool or process.
It is also critical to understand what the implications of the order of work are. Is doing one work package earlier on going to make subsequent work packages harder? For example, are restrictions on administrative privileges early on going to make deployment of other controls more difficult. Note, the prior point is just an example, where the risks and exposures of administrative privileges are manageable enough (through compensating controls, for example) that they can be accepted to reduce the friction of delivering other work packages.
Conclusion
At Trinity Cyber Security, we consider these factors and many more when developing an organisational specific roadmap. Please feel free to reach out to us on 1800 430 933 or email [email protected] to discuss how we can tailor a strategic roadmap for your organisation.