The Information Security Manual
By: Trinity Technical Assurance Team
Protecting sensitive information and ensuring the security of IT systems is a top priority for government agencies in Australia. Implementing Information Security Manual (ISM) controls for Active Directory (AD) is one way agencies can achieve this goal. However, maintaining effective ISM AD controls can be a complex and resource-intensive process. In this blog post, we’ll examine some of the details of ISM AD controls and the challenges involved in maintaining them to help government agencies in Australia better protect their IT systems and sensitive information.
The ISM is regularly updated by the ASD to reflect the latest threats and best practices in information security, and it is considered a valuable resource for organisations seeking to enhance their cybersecurity posture. The frequency of updates to the ISM can vary depending on the pace of change in the threat landscape and the availability of new guidance and resources. However, the ASD typically updates the ISM at least once a year, and sometimes more frequently if there are significant changes in the security environment. Organisations that rely on the ISM for their information security policies and practices should regularly check for updates and review their security measures to ensure that they remain effective and aligned with the latest guidance from the ASD.
Active Directory
The ISM provides a comprehensive set of policies and guidelines for managing information security risks, including those related to Active Directory (AD). AD is a critical component of many organisations’ IT infrastructure, and it is essential to ensure that it is secured appropriately to protect against unauthorised access and other security threats. The ISM provides specific guidance on how to protect Active Directory, including the following:
Access control: The ISM provides guidance on how to implement appropriate access controls to ensure that only authorized users can access and modify Active Directory resources.
Authentication and authorisation: Guidance on how to implement strong authentication and authorisation mechanisms to prevent unauthorised access to Active Directory resources.
Auditing and monitoring: Guidance on how to implement effective auditing and monitoring of Active Directory to detect and respond to security incidents and anomalies.
Secure configuration: Guidance on how to configure Active Directory securely, including applying appropriate security patches, disabling unnecessary services, and hardening the server configuration.
Backup and recovery: Guidance on how to implement effective backup and recovery procedures for Active Directory to ensure that critical data is protected and recoverable in the event of a security incident or outage.
ISM March 2023 AD Controls
1. Microsoft Active Directory Domain Services
Five new controls were added covering Microsoft Active Directory Domain Services (AD DS) domain controllers. These controls are generally for on-premise environments or where AD sync might be used with Azure. We will walk through each of them briefly below:
| Control | Title | Explanation | |
| ISM-1827
|
“Microsoft AD DS domain controllers are administered using dedicated domain administrator user accounts that are not used to administer other systems.”
|
Using dedicated domain administrator user accounts helps to prevent privilege escalation attacks, where an attacker gains administrative access to a system and then uses that access to gain administrative access to other systems in the network. By using a dedicated account for domain administration, the risk of compromising other systems in the network is minimised. This is generally already in place for many organisations. |
|
| ISM-1828
|
“The Print Spooler service is disabled on Microsoft AD DS domain controllers.”
|
The Print Spooler service is a potential attack surface and has been known to have vulnerabilities in the past. Disabling it on domain controllers helps to reduce the attack surface and mitigate the risk of exploitation. Multiple known exploits for this service exist, foe example: CVE-2021–1675, CVE-2021–34527, and CVE-2021–34481. This remediation for this issue is as straightforward as disabling the service on any machine that does not require it, including domain controllers. | |
| ISM-1829
|
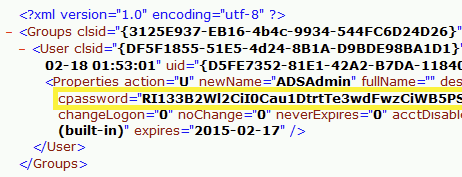
“Passwords and cpasswords are not used in Group Policy Preferences.”
|
Group Policy Preferences is a feature that allows administrators to configure various settings for users and computers in the domain. However, it has been known to store passwords in plain text or an easily reversible encrypted password, which can be easily retrieved by an attacker with access to the domain. Avoiding the use of passwords and cpasswords in Group Policy Preferences helps to reduce the risk of exposing sensitive credentials. These policies are stored in SYSVOL and are browsable by all users in Active Directory. Every policy file needs to be reviewed for this issue and an action plan on remediation decided for each of the impacted XML files. Below is a sample vulnerable GPP XML file.
|
|
| ISM-1830
|
“Security-related events for Microsoft AD DS are logged.”
|
Logging security-related events helps to detect and investigate potential security incidents. By monitoring the security logs, administrators can identify suspicious activity and take appropriate action before any damage is done. The events that can be captured have been extended by Microsoft to include advanced security events which need to be enabled and applied in Active Directory through the advanced audit policy configuration. | |
| ISM-1831
|
“Microsoft AD DS event logs are stored centrally.”
|
Storing event logs centrally provides a centralised view of all security events in the domain, making it easier to detect and investigate potential security incidents. This also prevents attackers from destroying or tampering with logs locally to make it more difficult to detect their path of compromise. |
2. Microsoft AD DS account hardening
Thirteen new controls were added covering Microsoft AD DS account hardening. These controls are generally for on-premise environments or where AD sync might be used with Azure. We will group these controls to highlight why they have been included and how they interact together:
| Controls | Titles | Explanation | |
| ISM-1835
ISM-1843
ISM-1844
|
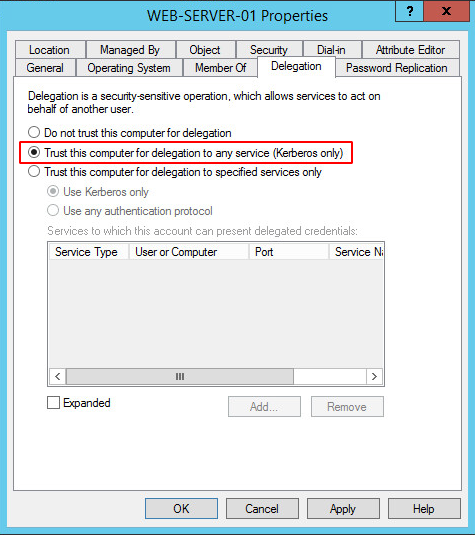
“Privileged user accounts are configured as sensitive and cannot be delegated.”
“User accounts with unconstrained delegation are reviewed at least annually, and those without an associated Kerberos SPN or demonstrated business requirement are removed.”
“Computer accounts that are not Microsoft AD SD domain controllers are not trusted for delegation to services.”
|
Unconstrained delegation is a feature in Active Directory that allows a service running on one computer to impersonate a user and access resources on other computers, without requiring the user to enter their credentials again. When configured improperly or granted to the wrong accounts, it can become a security risk and lead to several attacks, such as:
Reconnaissance: An attacker can use unconstrained delegation to gain access to sensitive information, such as user credentials and other sensitive data, from other computers on the network.
Delegation abuse: Attackers can use compromised accounts with unconstrained delegation to move laterally within the network and access sensitive systems or data. By reviewing accounts with unconstrained delegation and removing those without an associated Kerberos SPN or demonstrated business requirement, the attack surface for delegation abuse is reduced.
Trust abuse: Attackers can exploit trusted relationships between computer accounts to access resources that they would not otherwise have access to. By not trusting computer accounts that are not domain controllers for delegation to services, the attack surface for trust abuse is reduced.
Every user, computer account and service account in the domain must be reviewed for the these flags and decided if the minimum required privileges are applied. Often permission creep or simple mis-configuration during deployment has included an excessive delegation requirement.
|
|
|
ISM-1836
ISM-1834
ISM-1832
ISM-1833
|
“User accounts require Kerberos pre-authentication.”
“Duplicate SPNs do not exist within the domain.”
“Only service accounts and computer accounts are configured with Service Principal Names (SPNs).”
“Service accounts are provisioned with the minimum privileges required and are not members of the domain administrators group or similar highly privileged groups.”
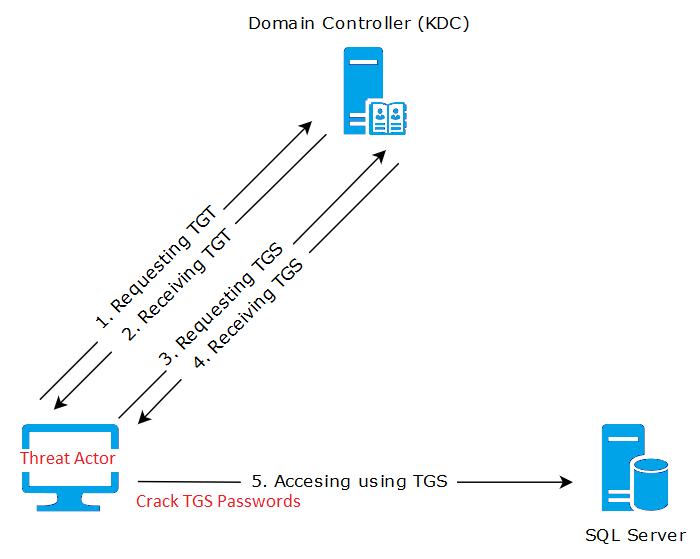
A simplistic kerberoasting example:
|
Trinity believes these controls are directly related to reducing Kerberos attacks. Kerberoasting is a vulnerability that affects the way that Windows Active Directory uses Kerberos authentication. Kerberos is a network authentication protocol that is used to provide secure communication over a non-secure network. In Active Directory, service accounts are often configured with a Service Principal Name (SPN), which is a unique identifier for a service running on a computer.
When a user wants to access a service that is protected by an SPN, the user’s computer requests a ticket-granting ticket (TGT) from the domain controller. The domain controller generates a TGT, which includes a session key that is used to encrypt and decrypt the user’s credentials. The TGT is then sent to the user’s computer, which uses the session key to decrypt the TGT and obtain a service ticket.
The vulnerability with Kerberoasting is that an attacker can request a service ticket for a service account with an SPN, and then use the ticket-granting ticket to crack the password hash for the service account. The attacker can then use the password to authenticate to the service and gain access to sensitive data.
There are several techniques that can be used to mitigate the risk of Kerberoasting attacks. One common approach is to limit the number of service accounts that are configured with SPNs, and to ensure that those accounts have strong, complex passwords. It is also important to ensure that service accounts are not members of highly privileged groups, and that they are provisioned with the minimum privileges necessary to perform their tasks.
Combining these controls with the above delegation restrictions would make a breach of a particular service account or Kerberos ticket extremely limited in scope and create a more difficult environment to use the obtained credentials for lateral movement. |
|
|
ISM-1841
ISM-1842
|
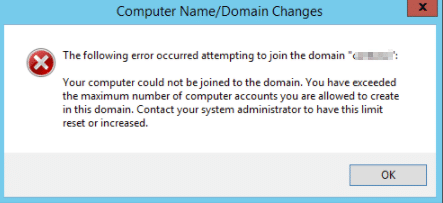
“Unprivileged user accounts cannot add machines to the domain.”
“Dedicated service accounts are used to add machines to the domain.”
|
The control “Unprivileged user accounts cannot add machines to the domain” is meant to prevent unauthorised users or malware from joining machines to the domain, which can lead to privilege escalation and compromise of domain resources. Without this control, an attacker could use a non-privileged account to add a malicious machine to the domain and gain access to domain resources. This is further compounded by issues such as ISM-1829 above, are in use.
Similarly, the control “Dedicated service accounts are used to add machines to the domain” helps prevent the misuse of privileged accounts for joining machines to the domain. If privileged accounts are used for this purpose, an attacker who compromises the account or its credentials could add malicious machines to the domain and gain access to sensitive resources.
To mitigate these risks, organisations should configure Active Directory to ensure that only dedicated service accounts can add machines to the domain. This can be accomplished by creating a separate service account for joining machines to the domain and assigning it the appropriate permissions. This service account can then be used for all machine joins, and access to it should be tightly controlled.
Additionally, organisations can use Group Policy to enforce the control that unprivileged users cannot add machines to the domain. All other accounts should be removed from this user right to prevent unauthorised machine joins. |
|
|
ISM-1838
ISM-1839
ISM-1840
|
“The UserPassword attribute for user accounts is not used.”
“Account properties accessible by unprivileged users are not used to store passwords.”
“User account passwords do not use reversible encryption.”
|
These controls are fundamental measures to ensure the overall health and security of Active Directory.
By ensuring that user account passwords have an expiration date and cannot be set to never expire or set without a password, this control helps ensure that passwords are regularly rotated, reducing the risk of a password being compromised and used by an attacker. Additionally, requiring a password for all user accounts reduces the risk of unauthorised access to resources and helps enforce accountability for actions taken by the user.
The UserPassword attribute is used to store passwords for user accounts in a way that is vulnerable to attack. By default, Active Directory does not use this attribute, but some applications or third-party software may use it to store passwords.
Some other properties in Active Directory are accessible by unprivileged users and can be used to store password information. This can include attributes such as description or comment. By ensuring that these properties are not used to store password information, the risk of unauthorised access to password information is reduced.
Reversible encryption is a method of storing passwords that can be easily decrypted, making it vulnerable to attack. This setting is a tick box in each users general properties. There may be business requirements for this configuration but it is generally not recommended.
All users active directory properties should be enumerated and reviewed for any legacy usage of these attributes. |
Summary
Effective ISM AD controls are essential for government agencies in Australia to protect their sensitive information and IT systems against cyber threats. However, maintaining these controls can be challenging without the right expertise and resources. If your agency needs assistance with ISM AD controls or other cybersecurity measures, consider partnering with a capable cybersecurity organisation. With their expertise and support, you can ensure that your agency is following the necessary security protocols and staying protected against evolving cyber threats.
Support
Trinity Security is dedicated to helping organisations protect their digital assets and prevent cyber attacks. Our team of experts have experience in assessing and securing Active Directory environments, and have a deep understanding of the potential vulnerabilities and attack vectors that threat actors can exploit. We have developed a comprehensive set of tooling and capabilities to detect, and remediate security issues in Active Directory, including all of the ISM controls outlined in this article.
Our tooling can identify potential issues such as password policies that do not adhere to best practices, misconfigured delegation settings, insecure Kerberos service tickets, and other common attack vectors. We provide detailed reports and recommendations for remediation, along with guidance on how to implement best practices to prevent future security incidents.
Whether you’re facing challenges with kerberoasting, delegation attacks, or any other potential security vulnerabilities within your Active Directory environment, our team has the expertise and capability to help you address them quickly and effectively.